Samsung Galaxy S25 Exploited by Researchers Using Five Zero-Day Vulnerabilities at Pwn2Own Ireland 2025
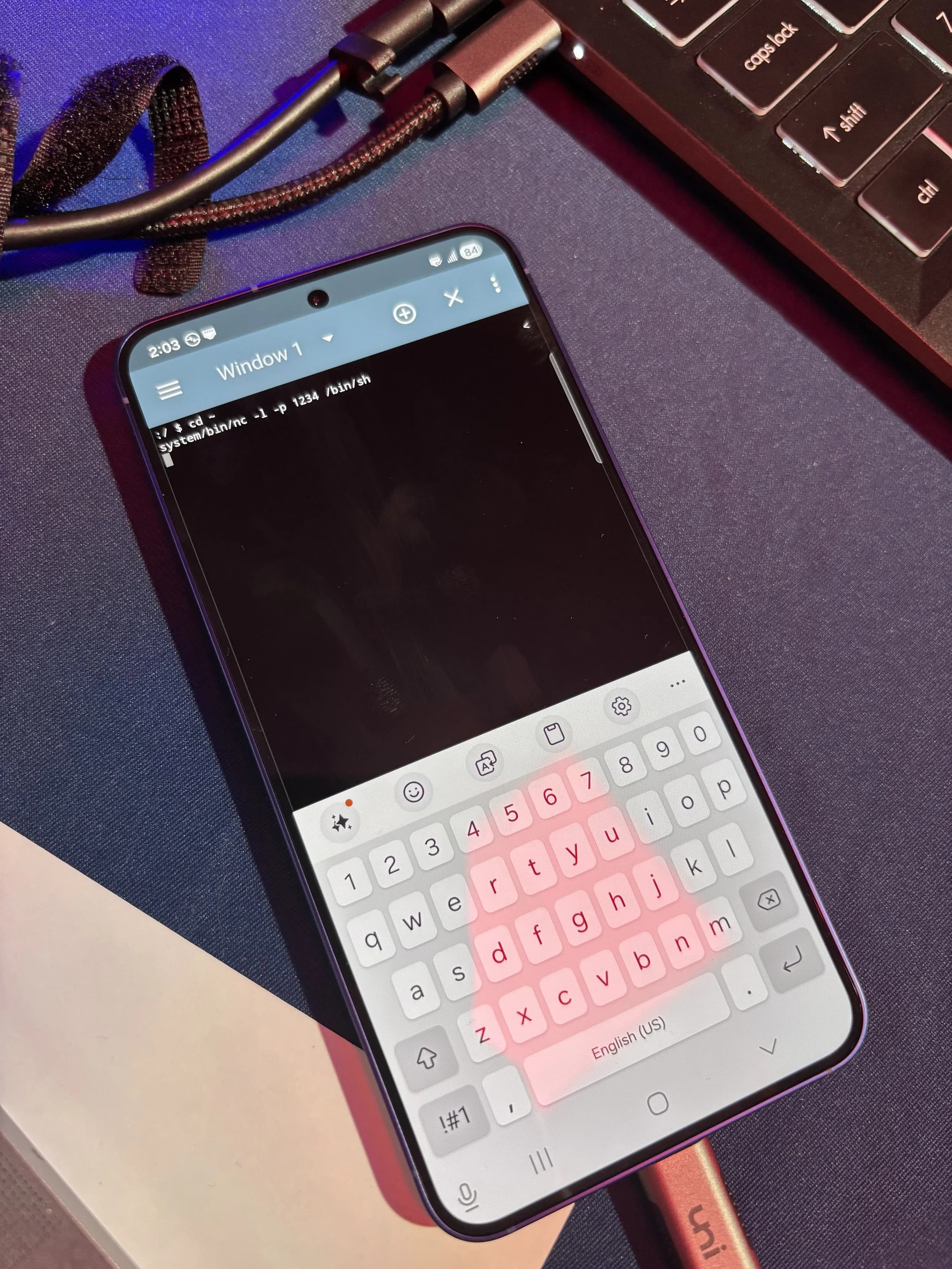
CORK, Ireland – Security researchers Ken Gannon of Mobile Hacking Lab and Dimitrios Valsamaras of Summoning Team successfully exploited the Samsung Galaxy S25 smartphone using a chain of five distinct zero-day vulnerabilities during day two of Pwn2Own Ireland 2025. The exploit, demonstrated on October 22, allowed them to gain significant control over the device from a single interaction, earning them $50,000 and 5 Master of Pwn points.
The Trend Zero Day Initiative (ZDI), organizers of the event, confirmed the successful hack via social media, stating, > "Wow - just wow. Ken Gannon (@yogehi) didn't just exploit the #Samsung Galaxy S25: he had it tell a joke, exfiltrate a picture, & open a shell. All that from a single click." This demonstration highlighted critical security flaws in Samsung's latest flagship device. The full exploit chain consisted of five different issues across several applications, enabling the installation of arbitrary APKs.
This achievement was a highlight of the Pwn2Own Ireland 2025 competition, which ran from October 21 to October 24. The event saw security researchers uncover a total of 56 unique zero-day vulnerabilities across various devices, with overall prize money reaching $792,750 by the end of the second day. The competition aims to identify and responsibly disclose vulnerabilities to vendors before malicious actors can exploit them.
Following the successful exploit, Gannon and Valsamaras will provide all details to Samsung in a "disclosure room." As per Pwn2Own protocol, vendors are given 90 days to develop and release patches for the discovered vulnerabilities before the ZDI publicly discloses the technical details. This process underscores the critical role of ethical hacking competitions in enhancing product security for consumers globally.