Critical Pre-Authentication RCE Vulnerability (CVE-2025-61757) in Oracle Identity Manager Deemed 'Trivial to Exploit'
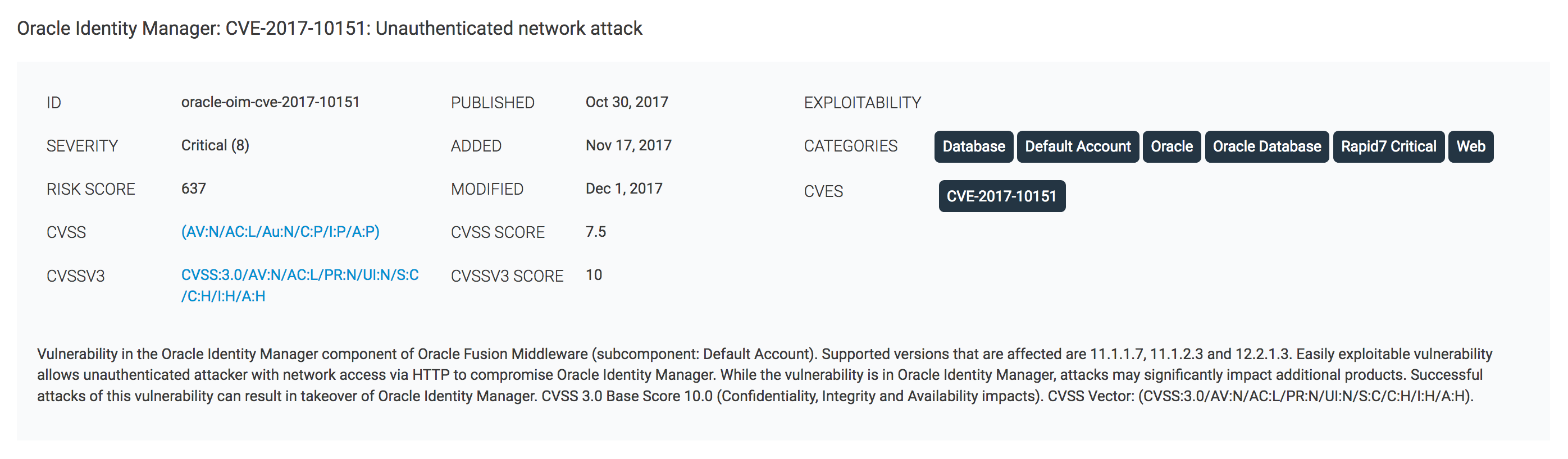
A critical pre-authentication Remote Code Execution (RCE) vulnerability, identified as CVE-2025-61757, has been discovered in Oracle Identity Manager (OIM), posing a significant threat to organizations utilizing the software. Cybersecurity firm Searchlight Cyber's research team publicly disclosed the flaw, describing it as "trivial to exploit" and capable of allowing unauthenticated attackers to compromise and gain full control over susceptible systems via HTTP network access. This discovery follows an earlier breach of Oracle Cloud's login service in January 2025, which compromised 6 million records and over 140,000 Oracle Cloud tenants.
The vulnerability was unearthed by Searchlight Cyber's Adam Kues and Shubham Shah, who noted that the flaw could have been used to breach the Oracle Cloud login service, which also ran OIM. The exploit leverages an authentication bypass mechanism within OIM's REST APIs, combined with a Groovy script compilation endpoint. Attackers can bypass authentication by manipulating request URIs with Java's path parameters, then use a Java annotation processor within a Groovy script to achieve RCE at compile time, even without direct script execution.
Oracle Identity Manager versions 12.2.1.4.0 and 14.1.2.1.0 are specifically affected by this critical flaw. The widespread adoption of Oracle Identity Management software by hundreds of enterprises and government entities means that a broad range of organizations could be at risk if patches are not promptly applied. The ease of exploitation makes this vulnerability particularly dangerous for unpatched systems.
Oracle has since addressed CVE-2025-61757 as part of its October 2025 Critical Patch Update, released on October 21st. The company strongly recommends that customers apply these security patches without delay to mitigate the risk of exploitation. Searchlight Cyber stated that their customers received "83 days of pre-emptive monitoring and protection from this vulnerability" before its public disclosure. The original tweet by "shubs" highlighted the severity, stating, "> Oracle Cloud was breached in Jan 2025 through vulns in Oracle Access Manager. @SLCyberSec's Research team found a new pre-auth RCE vulnerability in Oracle Identity Manager (CVE-2025-61757). This is a critical vulnerability and is trivial to exploit."